Agentic SDLC: The Rise of Self-Healing, Adaptive Software Systems
Explore the next evolution of the SDLC, moving beyond AI code generation to autonomous agents that monitor, diagnose, and remediate issues in deployed software, ushering in an era of self-healing systems.
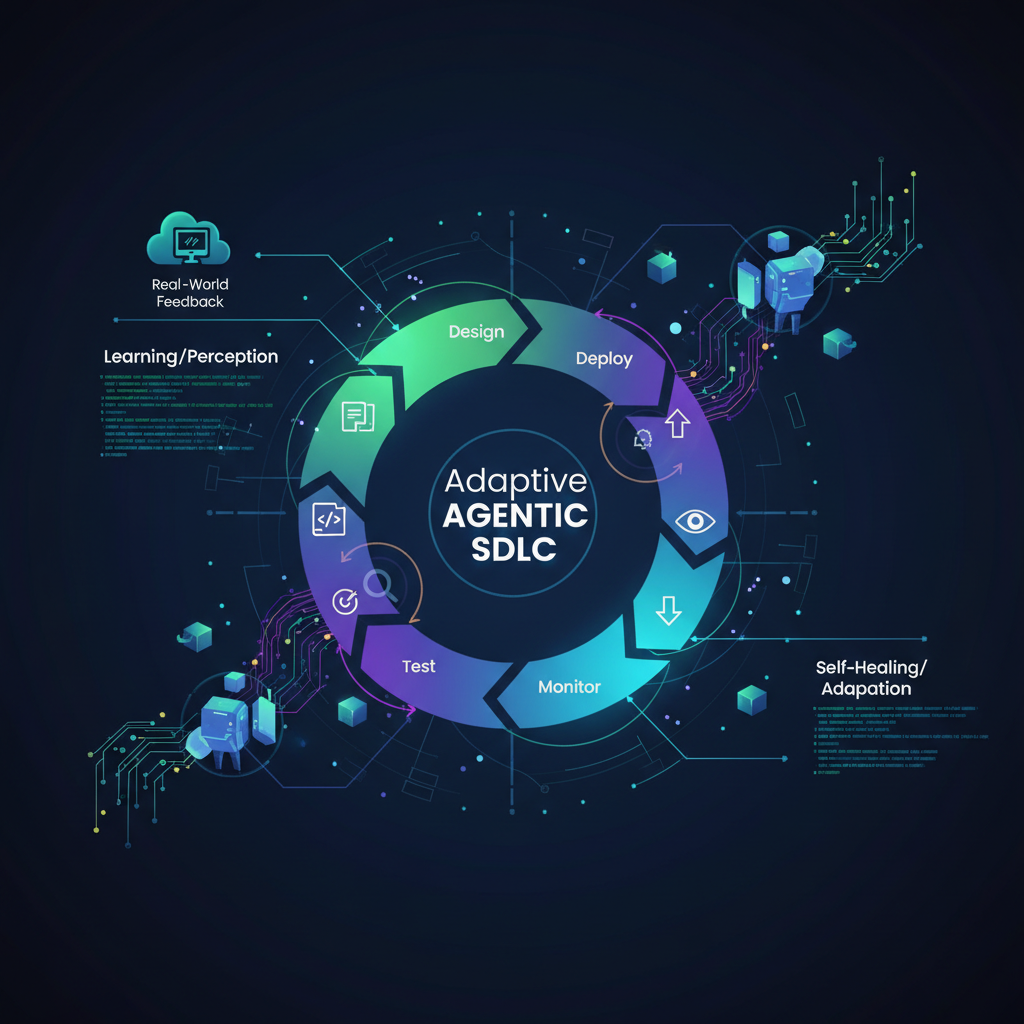
The software development lifecycle (SDLC) has undergone a profound transformation, evolving from manual, linear processes to agile, iterative methodologies. Now, with the advent of sophisticated artificial intelligence, we are on the cusp of another revolution: the Agentic SDLC. While initial explorations focused on AI agents generating code, tests, and documentation, the true frontier lies in empowering these agents to not just create software, but to monitor, diagnose, and automatically remediate issues within deployed systems. This paradigm shift, which we'll call Self-Healing and Adaptive Agentic SDLC, promises to usher in an era of autonomous system resilience, fundamentally altering how we build, maintain, and evolve complex software.
The Evolution from Code Generation to Autonomous Resilience
The journey of Agentic SDLC began with the promise of automating repetitive coding tasks. Large Language Models (LLMs) demonstrated remarkable capabilities in generating boilerplate code, translating natural language requirements into functional logic, and even writing comprehensive test suites. This initial wave significantly boosted developer productivity and accelerated development cycles.
However, the real-world challenges of software extend far beyond initial creation. Modern software systems are inherently complex, distributed, and dynamic. They operate in unpredictable environments, interact with myriad external services, and are subject to constant change. Manually debugging production issues, maintaining system health, and adapting to evolving requirements have become significant bottlenecks, consuming vast amounts of engineering effort and often leading to costly downtime.
This is where Self-Healing and Adaptive Agentic SDLC steps in. It represents the next logical evolution, moving beyond mere code generation to endow AI agents with the intelligence and agency to proactively and reactively manage the entire software lifecycle. The goal is to create systems that can not only identify their own problems but also formulate and execute solutions, adapting and evolving with minimal human intervention. This shift is driven by the urgent need to address software complexity, reduce operational overhead, and leverage the latest advancements in AI to build truly resilient systems.
The Pillars of Autonomous System Resilience
Achieving self-healing and adaptive capabilities requires a multi-faceted approach, integrating various AI techniques and architectural considerations. Let's break down the core components:
1. Autonomous Anomaly Detection & Monitoring
The foundation of any self-healing system is its ability to perceive its own state. This involves agents continuously monitoring a vast array of data sources:
- System Logs: Agents leverage LLMs to perform semantic understanding of unstructured log data. Instead of just looking for keywords or error codes, LLMs can interpret the context and meaning of log entries, identifying subtle patterns or unusual sequences that might indicate an impending issue, far beyond simple thresholding. For instance, an LLM might infer a database connection issue not just from an explicit "connection refused" error, but from a series of slow query logs followed by intermittent timeouts across multiple services.
- Metrics & Traces: Traditional monitoring tools provide quantitative data (CPU usage, latency, error rates). Agents integrate with these systems, using machine learning models (e.g., time-series forecasting, clustering algorithms) to establish baselines and predict anomalies before they manifest as critical failures. Predictive anomaly detection can anticipate resource exhaustion or performance degradation hours in advance.
- User Feedback & External Signals: Agents can monitor bug reports, support tickets, social media mentions, and even internal communication channels. LLMs can process this natural language data to identify emerging issues, prioritize problems based on sentiment or impact, and correlate user-reported symptoms with internal system states. Imagine an agent noticing a spike in "login failed" complaints on Twitter and cross-referencing it with authentication service logs, even if no explicit error threshold has been breached yet.
This continuous, intelligent monitoring acts as the system's nervous system, providing real-time awareness of its health and performance.
2. Intelligent Diagnosis & Root Cause Analysis (RCA)
Once an anomaly is detected, the next critical step is to understand why it occurred. This is where intelligent diagnosis comes into play, moving beyond simple symptom-matching to deep root cause analysis.
- Data Correlation and Fusion: Agents correlate diverse data sources that human operators often struggle to connect manually. This includes code changes from version control, deployment history, infrastructure events (e.g., node failures, network changes), runtime metrics, and even architectural diagrams and documentation. An agent might link a sudden increase in latency to a recent code deployment that introduced an inefficient database query, which in turn was triggered by a specific user interaction pattern.
- LLM-Powered Reasoning: LLMs are instrumental in "reasoning" about potential causes. Given a set of symptoms and correlated data, an LLM can generate hypotheses based on its understanding of system knowledge (codebase, architecture, common failure modes). It can then use this reasoning to formulate targeted queries to observability platforms, simulate scenarios in a sandbox environment, or even propose specific probes to gather more diagnostic information. For example, if a microservice is failing, an LLM might deduce, "Given the symptoms (HTTP 500s, high CPU) and recent code changes to the
PaymentProcessorservice, the issue could be an infinite loop in thecalculate_taxfunction, especially if thecountry_codeinput is malformed." - Causal Inference: Advanced agents can employ causal inference techniques to establish cause-and-effect relationships, distinguishing between correlation and causation. This is crucial for identifying the true root cause rather than merely addressing a symptom.
3. Automated Remediation & Self-Healing
The ultimate goal of self-healing is to automatically resolve issues. This is perhaps the most challenging and impactful aspect, requiring agents to not only understand problems but also to act upon them.
- Code Patch Generation: This is a direct extension of code generation. For identified bugs or vulnerabilities, agents can propose and generate code fixes. This can range from simple configuration adjustments (e.g., increasing a timeout value, modifying a database connection string) to generating complex logic patches. For instance, if an agent diagnoses an off-by-one error in a loop, it could generate a precise code diff to correct it.
- Deployment & Rollback: Agents can automatically deploy generated patches or configuration changes. Crucially, they can also initiate rollbacks to previous stable versions if a new deployment introduces further issues, adhering to predefined policies or learned safe deployment strategies. This requires robust integration with CI/CD pipelines and infrastructure-as-code tools.
- Configuration Management: Agents can adapt system configurations dynamically. This might involve scaling resources up or down based on load, adjusting database parameters for optimal performance, or reconfiguring network settings to bypass a failing component.
- Test Case Generation & Validation: Before deploying any fix, agents can automatically generate new test cases specifically designed to validate the fix and prevent regressions. These tests are then integrated into the CI/CD pipeline, ensuring that the proposed solution doesn't introduce new problems. This closes the loop, ensuring the quality and safety of automated changes.
4. Adaptive System Evolution
Beyond reactive self-healing, agents can drive proactive adaptation and continuous improvement, leading to truly resilient and optimized systems.
- Proactive Optimization: Agents continuously analyze system performance data, identifying bottlenecks or inefficient code patterns even when no explicit failure has occurred. They can then propose and potentially implement optimizations, such as suggesting indexing strategies for a database, refactoring a slow API endpoint, or optimizing resource allocation in a Kubernetes cluster.
- Requirement Adaptation: This is a more advanced capability where agents monitor user behavior, system performance, and external trends to identify implicit user needs or evolving requirements. They might suggest minor feature adjustments, UI improvements, or even implement small, data-driven changes to better align the system with user expectations. For example, if an agent observes a high drop-off rate at a specific step in a user journey, it might suggest A/B testing a simpler alternative or even autonomously implement a minor UI tweak.
- Security Posture Management: Agents continuously scan for new vulnerabilities (CVEs), identify affected code within the system, generate patches, and adapt security configurations (e.g., firewall rules, access policies) to maintain a robust security posture. This proactive defense is critical in today's threat landscape.
Human-in-the-Loop & Trust: The Critical Interface
While the vision is autonomous, human oversight remains paramount, especially in the early stages of this technology. Building trust and ensuring safety are non-negotiable.
- Defining Autonomy Boundaries: Organizations must define clear policies for agent autonomy. For critical changes (e.g., production code modifications, large-scale infrastructure changes), human approval might be required. For less critical or well-understood issues, full autonomy might be granted.
- Human Oversight & Intervention: Mechanisms for human developers and operators to monitor agent activities, intervene, and override decisions are essential. This could involve dashboards showing agent actions, alert systems for proposed changes, and kill switches for emergency situations.
- Explainable AI (XAI): For agents to earn trust, they must be able to explain their reasoning. XAI techniques enable agents to justify their diagnoses and proposed actions in human-understandable terms. An agent proposing a code fix should be able to articulate why it believes that fix is necessary, how it arrived at that conclusion, and what potential side effects it considered.
- Feedback Loops: Agents must learn from human corrections, approvals, and rejections. Every human intervention becomes a valuable data point for refining the agent's models and decision-making processes. This continuous feedback loop is vital for improving agent performance and reliability over time.
Architectural Considerations for Multi-Agent Systems
Implementing Self-Healing and Adaptive Agentic SDLC requires a robust architectural foundation, often involving a multi-agent system design.
- Specialized Agents: Instead of a single monolithic agent, a system typically comprises multiple specialized agents. For example:
- Monitor Agent: Focuses on data collection and anomaly detection.
- Diagnosis Agent: Correlates data, performs RCA, and generates hypotheses.
- Planning Agent: Develops remediation strategies based on diagnoses.
- Patch Agent: Generates code fixes or configuration changes.
- Deployment Agent: Manages the deployment and rollback of changes.
- Test Agent: Generates and executes validation tests. These agents communicate and collaborate, forming a distributed intelligence system.
- Integration with Existing Ecosystems: Seamless integration with existing DevOps tools, CI/CD pipelines (e.g., Jenkins, GitLab CI, GitHub Actions), observability platforms (e.g., Datadog, Prometheus, Grafana), version control systems (e.g., Git), and infrastructure-as-code tools (e.g., Terraform, Ansible) is crucial. Agents need to operate within and leverage the existing technological landscape.
- Secure Execution Environments: Since agents might perform sensitive operations (e.g., modifying production code, accessing critical infrastructure), they must operate within secure, isolated environments with strict access controls and auditing capabilities.
Practical Applications and Use Cases
The theoretical benefits of Self-Healing and Adaptive Agentic SDLC translate into tangible, high-impact practical applications:
- Automated Bug Fixing in Production: Imagine a critical e-commerce service experiencing intermittent checkout failures. An agent detects the anomaly, correlates it with a recent database schema change, diagnoses a mismatch in a data type, generates a code patch to correctly cast the value, runs automated tests, and deploys the fix – all within minutes, minimizing lost revenue and customer frustration.
- Proactive Performance Tuning: An agent observes a gradual increase in query latency for a specific microservice. It analyzes database logs, identifies an unindexed column being heavily queried, proposes adding an index, and automatically applies the schema change during off-peak hours, preventing a future performance bottleneck.
- Security Vulnerability Remediation: A new CVE is announced for a popular library. An agent scans the codebase, identifies all instances where the vulnerable library is used, generates patches to upgrade the library or apply specific workarounds, and initiates a CI/CD pipeline to test and deploy the fix across all affected services.
- Adaptive Microservice Orchestration: In a complex microservices architecture, an agent continuously monitors service health, traffic patterns, and resource utilization. If one service becomes overloaded, the agent can automatically scale out instances, reroute traffic to healthy services, or even temporarily degrade non-critical functionality to maintain overall system stability.
- Self-Improving Test Suites: A production incident occurs due to an edge case not covered by existing tests. The diagnosis agent identifies the specific conditions that led to the failure. A test agent then automatically generates a new unit test and an integration test covering this exact scenario, adding it to the project's test suite to prevent future regressions.
Challenges and Future Directions
While the promise is immense, the path to fully autonomous, self-healing systems is fraught with challenges:
- Safety and Reliability Guarantees: How can we mathematically prove or rigorously test that agent-generated fixes will not introduce new, potentially worse bugs or security vulnerabilities? This is perhaps the most critical challenge, requiring robust verification mechanisms and formal methods.
- Complexity of Reasoning: Moving beyond simple, localized fixes to understanding and remediating complex architectural interactions, emergent behaviors in distributed systems, and subtle logical flaws remains a significant hurdle for current AI models.
- Learning from Failure: Agents need to effectively learn from past remediation attempts, both successful and unsuccessful, to refine their strategies. This requires sophisticated reinforcement learning techniques and the ability to generalize from limited failure data.
- Data Scarcity for Training: Generating diverse and realistic training data for complex diagnostic and remediation tasks, especially for rare or novel failure modes, is a major challenge.
- Ethical Implications: Who is ultimately responsible when an autonomous agent introduces a critical bug, causes a security breach, or makes a decision with unintended consequences? This raises profound questions about accountability, liability, and the role of human oversight.
- Regulatory Compliance: How do self-healing systems interact with stringent regulatory requirements (e.g., GDPR, HIPAA, SOX) that mandate detailed audit trails, change management processes, and human approval for critical system modifications? Ensuring compliance while maintaining autonomy will require careful design.
Conclusion: Towards a Resilient Future
Self-Healing and Adaptive Agentic SDLC is not just an incremental improvement; it's a fundamental shift in how we conceive and manage software systems. It moves us closer to a future where software is not merely a static artifact but a dynamic, intelligent entity capable of perceiving, reasoning, and acting upon its own environment.
By leveraging the power of LLMs, reinforcement learning, and multi-agent systems, we can build software that is inherently more resilient, adaptable, and efficient. While significant challenges remain, particularly around safety, trust, and ethical considerations, the potential rewards – reduced downtime, faster incident response, lower operational costs, and accelerated innovation – are too compelling to ignore. This emerging field represents a rich tapestry for research, development, and practical implementation, paving the way for truly autonomous and robust software ecosystems that can thrive in an increasingly complex digital world.